Data Quality Monitoring
Trust Your Data
Anomalo’s automated AI ensures rapid detection, root cause analysis, and resolution of data quality issues, enabling quick mitigation before impacting your operations. Feel confident in your data by finding the root cause before anyone else.
Trusted by Industry Leaders
Data quality monitoring platform
Anomalo is the easiest way to continuously monitor all your enterprise data, without writing a single line of code.
1.
Connect your data sources
Integrate Anomalo with your enterprise data lake/warehouse in one click. To monitor data in transit, connect Anomalo to data orchestrators and ETL tools.
2.
Turn on AI data quality monitoring
Start detecting potential data quality issues across all your tables automatically. Unsupervised machine learning deeply understands your data, including hidden correlations, expected delivery times, and seasonal changes.
3.
Add validation rules and KPIs
Beyond the built-in checks, it’s easy for everyone to add custom data validation rules and track key metrics with a no-code UI or API.
4.
Detect, alert, and resolve
Quickly address data quality issues with Anomalo’s notifications, automated root-cause analysis, and data lineage.
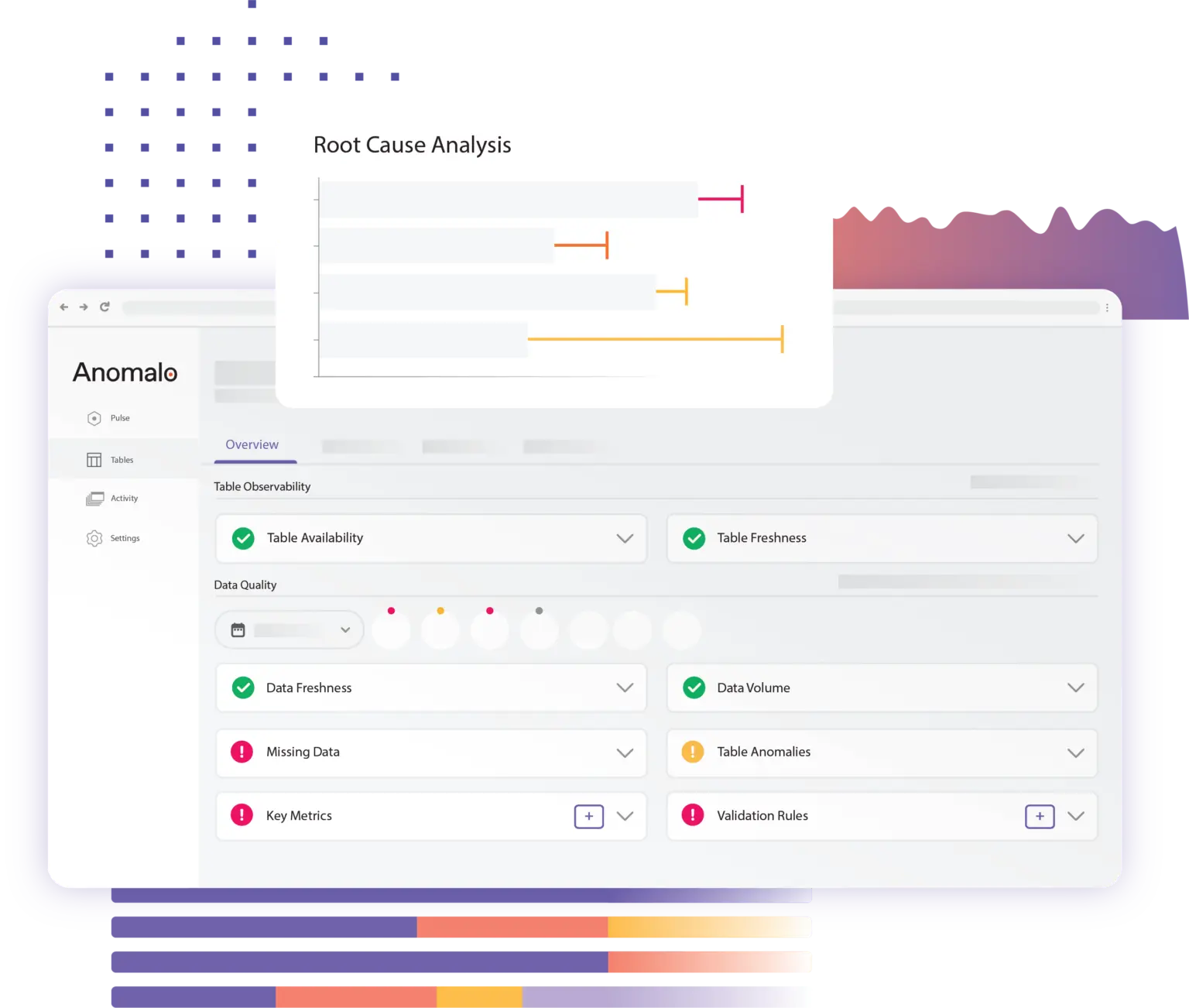
Monitoring Data Quality
Data Quality Monitoring Powered by AI
Go beyond data observability with robust data quality monitoring you can trust.
- Powerful data quality checks use unsupervised machine learning to monitor data values
- Automatically identify missing, late, incomplete, and anomalous data
- Sophisticated alert routing with intelligent false positive suppression
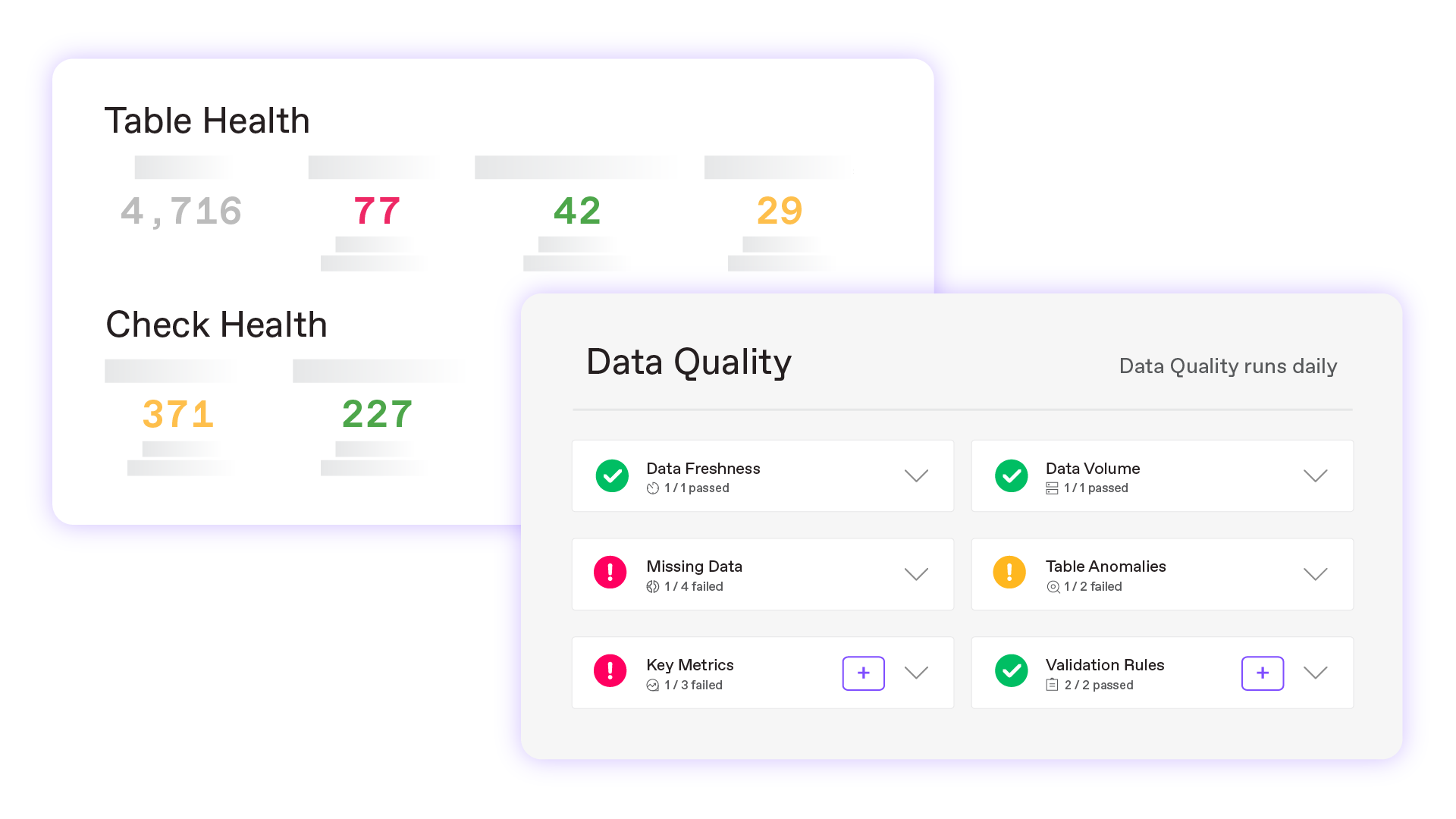
Data Quality Monitoring Solution
Built for Enterprise Scale
Effortlessly monitor thousands of tables and billions of records
- Cost-effective data quality monitoring with easy bulk configuration and efficient scheduling
- Secure in-VPC deployment, SOC 2 compliant
- Integrate with data catalogs and generate executive reports
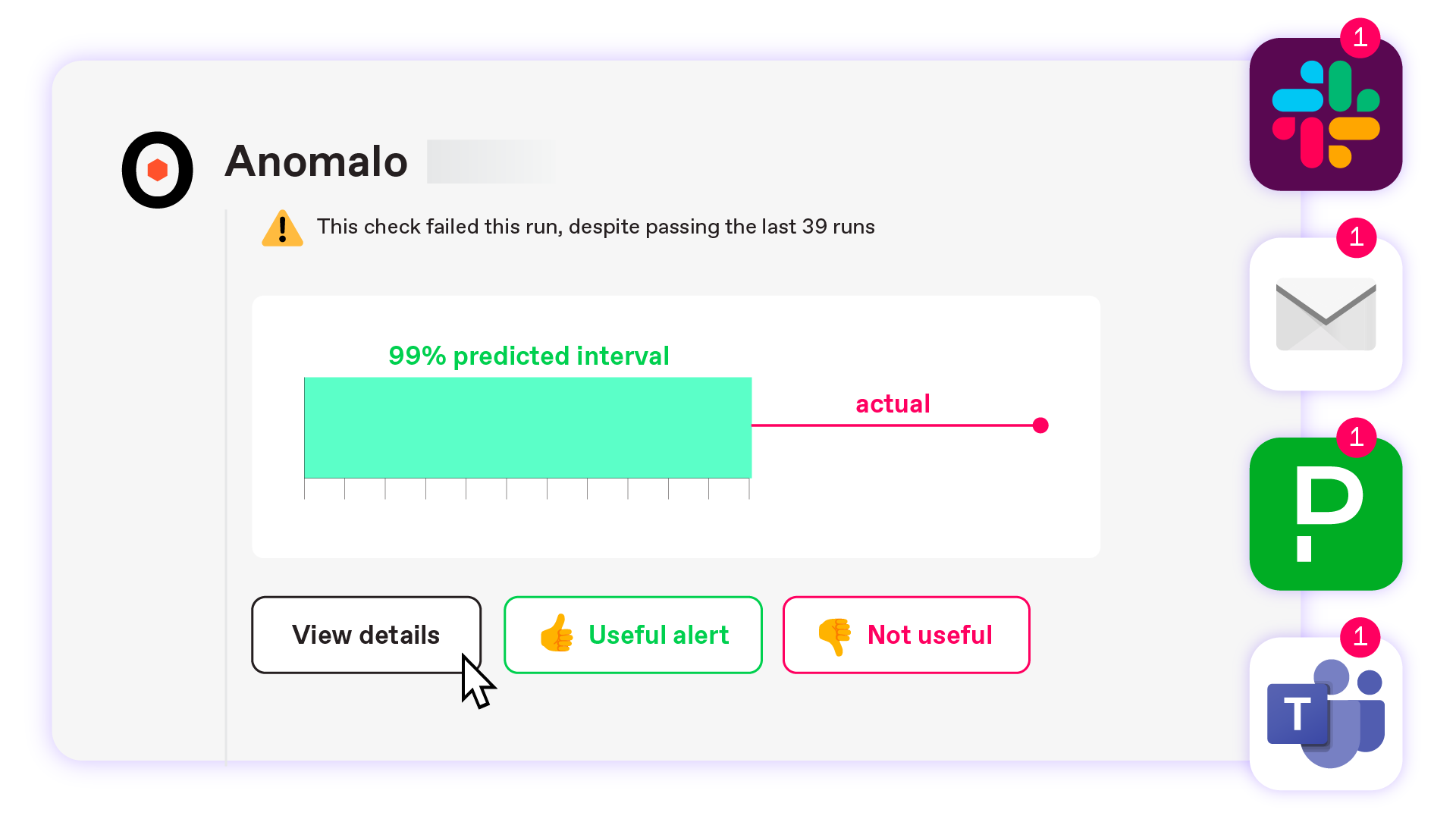
Data Quality Improvement
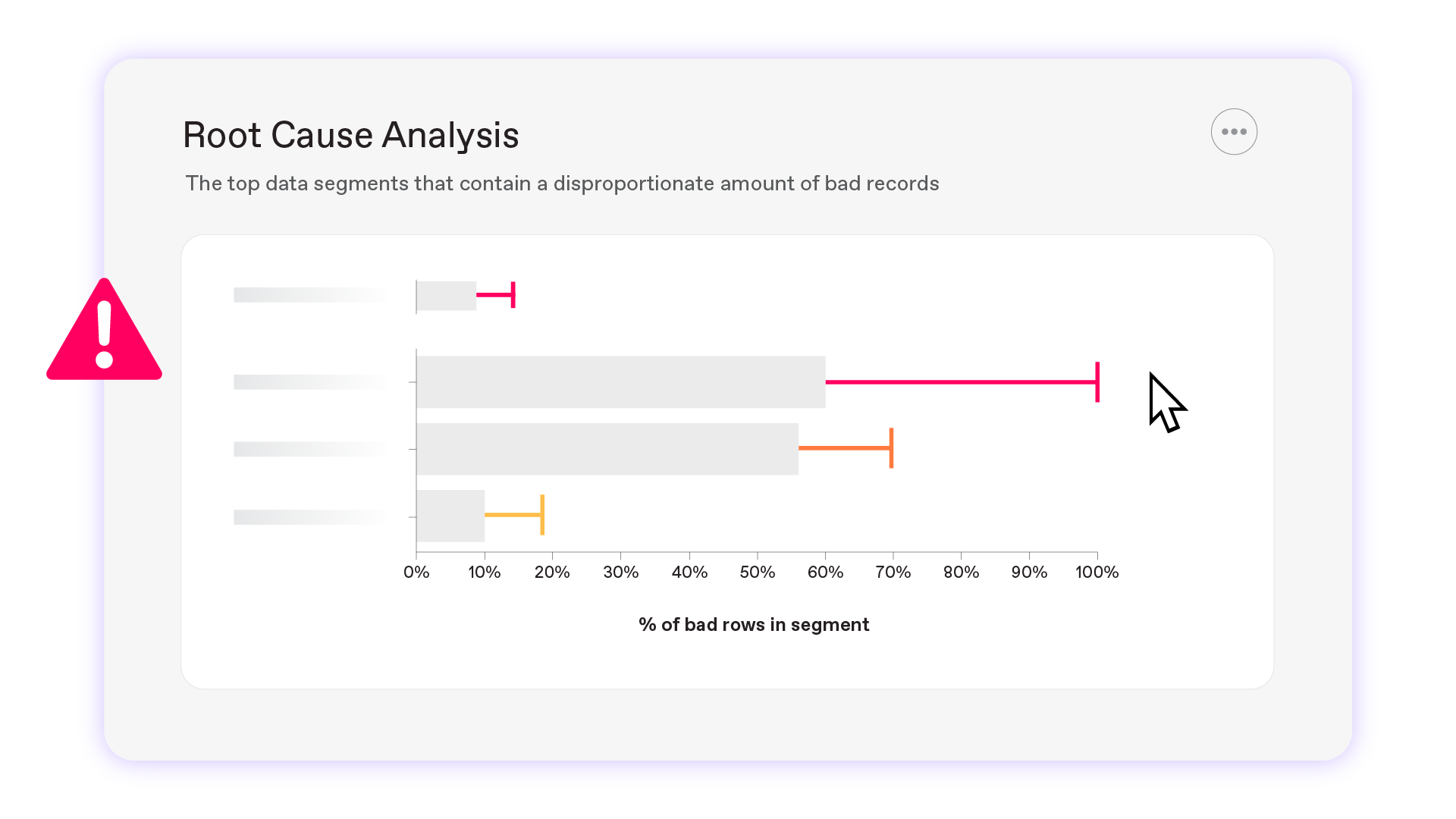
Automated Root Cause Analysis
See the severity, impact, and likely cause of an issue, saving hours on investigation.
- Samples and visualizations for deep analysis and data profiling
- Triage and resolution workflows that integrate with your ticketing system
- Automatic upstream and downstream lineage
Anomalo Data Proof Points
Anomalo is differentiated in its AI-first approach to data quality
“Data is critical to the life blood of enterprises and data quality problems are real. IDC research consistently shows that there is a lack of trust in data, with data management and improvement being a high priority investment as we enter into the era of AI Everywhere,” said Stewart Bond, research vice president, Data Intelligence and Integration Software research at IDC.
“Anomalo is differentiated in its AI-first approach to data quality. Anomalo automatically builds ML models for each dataset based on the history, patterns and structure of the data, and these models can spot when issues arise in the data, enabling pro-active data quality resolution which can result in improved operations, analytics and AI, leading to better business outcomes.”
Stewart Bond, Research Vice President, Data Intelligence and Integration Software research at IDC
Anomalo works with your data stack
Partners

Integrations
Our Customers
What Customers Say
Featured Resources
Learn more about how Anomalo delivers best-in-class enterprise data quality monitoring.
FAQ
Frequently Asked Questions
If you have additional questions, we are happy to answer them.
What kind of custom data quality monitoring does Anomalo offer?
While Anomalo’s automation offers immense value out of the box, you can also set user-defined validation rules or track specific business metrics for your key tables. You can do all of that from Anomalo’s UI, without even needing to write code. If you need more control, write checks in SQL or even integrate with our API to migrate existing checks.
What data quality monitoring techniques does Anomalo utilize?
Anomalo uses a mix of data quality monitoring techniques to ensure coverage across your entire data warehouse. First, you can set up low-cost, metadata-based data observability monitoring for all your tables to ensure on-time delivery and completeness. Then, for the tables where you want to additionally monitor the data values themselves, you can set up Anomalo’s automated data quality checks, including AI-based anomaly detection. This uses unsupervised machine learning to learn the historical patterns in your data and look for unexpected changes or poor data quality. Finally, for tables where you want even more custom monitoring, you can set up user-defined validation rules and track key metrics.
Why is data quality monitoring important?
Data quality monitoring is essential to ensure that bad data doesn’t lead to poor business outcomes. Low-quality data can cause all kinds of problems, from broken products and user experiences, to inaccurate dashboards and reports, to machine learning and generative AI models that behave erratically. Data quality monitoring is important for compliance and data governance as well. Furthermore, if your business users don’t believe that they can rely on your data, they are less likely to make data-driven decisions. Without data quality monitoring, you may end up investing a lot of time and resources to modernize your data stack, only to find that your efforts to get value from your data are blocked by inconsistency, inaccuracy, and overall lack of trust.
How does Anomalo ensure data quality at scale?
To offer data quality coverage for any data warehouse, even with tens of thousands of tables, Anomalo provides a suite of data quality checks. First, we offer data observability checks, which are a low-cost way to monitor your entire warehouse using table metadata. From there, you can configure tables to automatically measure data quality in one click. Automated data quality checks go deeper than observability to sample and inspect the data values themselves. You can also track KPIs about your data to identify trends and changes in segments. Finally, for that subset of key business tables where you need to write strict validation rules that your data must conform to, you can define those in Anomalo’s UI.
For most businesses, it’s impossible to write rules about every column and every table. That’s why Anomalo’s algorithms use AI/machine learning to understand patterns, set thresholds, and know when to alert. These algorithms learn and adapt as your data grows and changes over time.
Does Anomalo provide data profiling and analysis?
We do. Tables that are configured for data monitoring in Anomalo can display visual data profiling information, such as the distribution of data values in each column. Furthermore, each data quality check offers rich visualizations to understand why and how your data is passing or failing. For additional analysis, you can monitor key metrics about your data, which will generate more charts for exploration and notify you when there are significant changes.
Does Anomalo provide data lineage tools?
Yes! For each table that you monitor in Anomalo, you can see data lineage information that is pulled directly from your data warehouse/lakehouse, including a mapping of how data flows upstream and downstream. This can be very helpful with diagnosing data issues and understanding the potential impact of any failures.
Get Started
Meet with our expert team and learn how Anomalo can help you achieve high data quality with less effort.